By Tim Irnich, Chair, OPNFV Technical Steering Committee and Program Manager, Cloud, Open Source & Ecosystem at Ericsson
Today, the Fraser release goes live. It’s an important milestone for OPNFV, and I would like to sincerely thank all contributors, PTLs and working group facilitators, TSC members, Linux Foundation staff and all other supporters for the tremendous effort, creativity, enthusiasm and skill that went into the release.
 Fraser Highlights
Fraser Highlights
OPNFV is a large and diverse project and it is impossible to list all achievements in one blog post. But just to mention a few highlights, Fraser provides a significant step towards more mature cloud native support, higher platform maturity by enhancing features like telemetry and high availability, more robust networking capabilities and various forms of data plane acceleration, and also significantly advanced–and in some cases introduced–entirely new test methodologies and tools. As with previous OPNFV releases, Fraser integrates and verifies lots of updated and upgraded upstream components like OpenStack Pike, ODL Oxygen, FD.io release 18.01, and Kubernetes 1.9, only to mention a few. We have also made significant progress with our range of artifacts and services targeting developers by providing easily deployable, flexibly composable, and up-to-date platforms that can be used as comprehensive yet accessible development and testing environments.
The adoption of cloud native in OPNFV, in terms of creating reference stacks based on Kubernetes and integrating them with other related components, as well as the related enhancements to our CI and testing infrastructure, started some time ago. The Fraser release denotes a significant step forward in this effort. For example, we now have 8 different deployment scenarios across various installers that integrate Kubernetes and related components and tools, and Kubernetes support has been added to both Functest and Yardstick test frameworks.
Advances in testing include increased test coverage; for example in the areas of high availability and long term stability, better usability through lower execution times and additional traffic generators, and better consumability through separating generic framework components from OPNFV-specific code. Based on the observation that the OPNFV test frameworks and the underlying infrastructure for test data collection and analytics is a useful asset also for other projects, the Functest team has introduced a clean separation between test framework and the related packaging mechanisms on the one side and OPNFV test cases on the other side. This allows cross-community testing where the Functest test framework, test results API and database backend, and visualization dashboards can be used by other projects within LFN and beyond. This has seen immediate adoption in ONAP with the interesting side effect that a 100MB container could replace the 1GB VM that was used previously, and reusing the remaining OPNFV CI pipeline becomes very simple. Another noteworthy enhancement is that VSPERF added new tests to measure data plane performance in “noisy neighbor” situations–an effect known to cause significant performance degradations in suboptimally configured systems.
Further enhancements highlighting the growing maturity of the OPNFV reference platform are infrastructure maintenance and upgrade with zero VNF downtime, new and updated collectd plugins data collection plugins including DPDK and OVS stats & events, an SNMP agent, IPMI events and many more. The Calipso project provides networking discovery, visualization, monitoring and analysis in Kubernetes and has added support for Contiv/VPP and Flannel in Fraser. The SDNVPN project has added support for Equal Cost Multipath routing (ECMP) in order to overcome the bottleneck of using a single VxLAN tunnel between datacenter edge and fabric.
Developers Tools
Our Cross-community CI (XCI) initiative is becoming more mature and has seen a boost in adoption by other projects during the Fraser release. It now supports multiple scenarios and a number of OPNFV features like BGPVPN, Service Function Chaining and Kubernetes have been integrated. We have also seen other installer toolchains like Apex adopting the XCI concept.
We have launched our Lab-as-a-Service offering (available at http://labs.opnfv.org), which takes this concept behind XCI to the next level by providing free access to hardware resources and pre-provisioned stacks, saving community developers of OPNFV and other projects significant time and effort and enabling them to dedicate significantly more time to things that actually matter to them. We are continuing to work on this and will have even more information to share in the coming months.
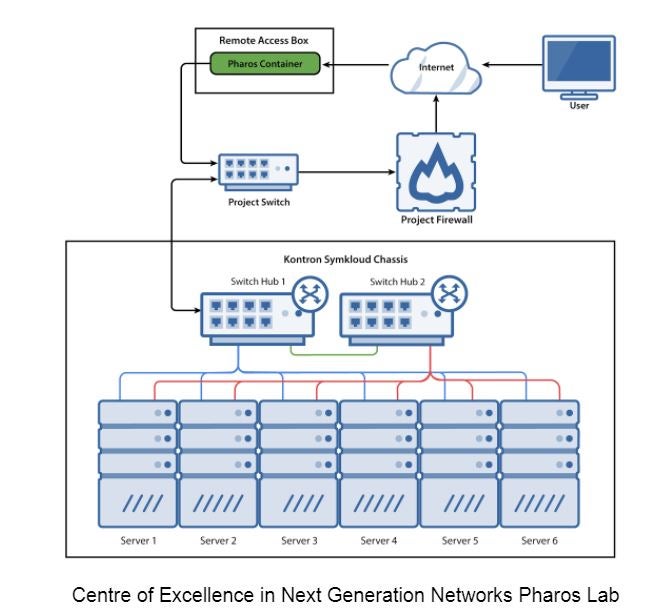
Moreover, with Fraser, the vision towards dynamic continuous integration (CI) got a boost with the introduction of Scenario Descriptor File (SDF), Pod Descriptor File (PDF), and Installer Descriptor File (IDF) specifications, which contain machine readable information to enable OPNFV installers to deploy any OPNFV scenario to any Pharos lab. With these descriptor files, CI jobs can dynamically run on any available hardware as long as the SDF and IDF requirements match PDF capabilities. The concept will roll out in several phases over the summer.
Looking Ahead
We’ll put the Fraser release to the test in June at the Fraser Plugfest co-located with ETSI at their facilities in Sophia Antipolis, France and are already several milestones into Gambia where we will add a CD-based release process. Cloud native and edge computing will further advance through collaboration with upstream components in CNCF, updated lab specifications in Pharos suitable for edge computing along with new projects requirements, upstream development, and end-to-end testing and integration.
At 3 ½ years in, OPNFV is certainly growing more and more mature in its core deliverables whole at the same time looking ahead and addressing new use cases like Cloud Native and Edge Computing. Participation and adoption by end users like China Mobile and Orange further defines the important role OPNFV is playing in the industry. I hope you’ll join us!


 The fourth OPNFV Plugfest, hosted by Intel at their Jones Farm Campus outside of Portland, OR was held on December 4-8, 2017. Intel has been a key contributor to OPNFV since the project launch and their hospitality was certainly appreciated by everyone attending the event. It was also great to see Intel’s Pharos PODs up close as they have been a great resource for the OPNFV community. There were 104 attendees (up 20% from last time), from 30 organizations that included 6 end-users and 6 non-member companies.
The fourth OPNFV Plugfest, hosted by Intel at their Jones Farm Campus outside of Portland, OR was held on December 4-8, 2017. Intel has been a key contributor to OPNFV since the project launch and their hospitality was certainly appreciated by everyone attending the event. It was also great to see Intel’s Pharos PODs up close as they have been a great resource for the OPNFV community. There were 104 attendees (up 20% from last time), from 30 organizations that included 6 end-users and 6 non-member companies. As we kick off 2018, the OPNFV Compliance & Certification committee—the members driven body within OPNFV that defines recommendations to the Board for policies and oversight for compliance and certification—is pleased to
As we kick off 2018, the OPNFV Compliance & Certification committee—the members driven body within OPNFV that defines recommendations to the Board for policies and oversight for compliance and certification—is pleased to  It is with gratitude and pleasure that I look back on our accomplishments of 2017 and with excitement for the future as I look ahead to our path as part of LF Networking in 2018. We have come such a long way together since our founding over three years ago and this moment of transition marks a great opportunity to reflect on our impact.
It is with gratitude and pleasure that I look back on our accomplishments of 2017 and with excitement for the future as I look ahead to our path as part of LF Networking in 2018. We have come such a long way together since our founding over three years ago and this moment of transition marks a great opportunity to reflect on our impact.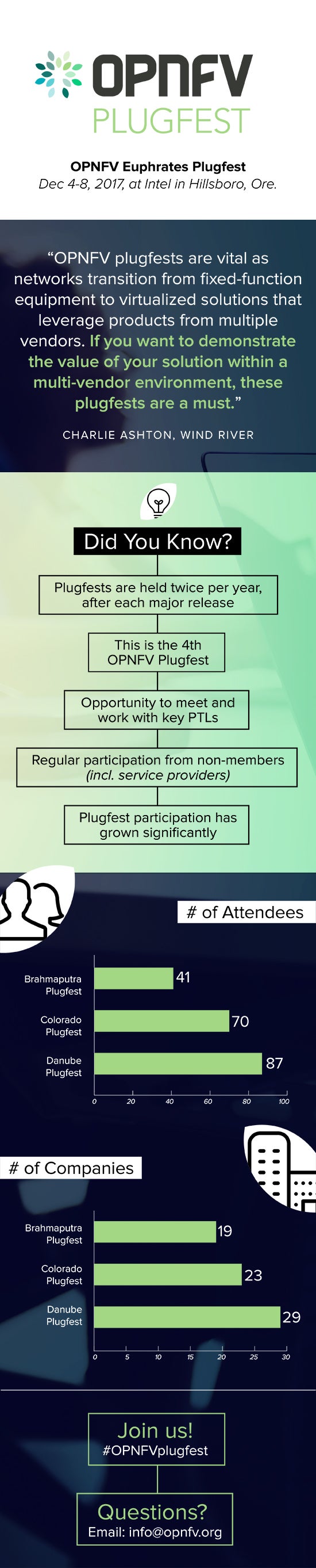
 Three years after its founding, OPNFV has carved out a solid niche in the industry as an NFV center of gravity, as an integrator of upstream projects, and as the standard software testing platform.
Three years after its founding, OPNFV has carved out a solid niche in the industry as an NFV center of gravity, as an integrator of upstream projects, and as the standard software testing platform.