This month marks our two-year anniversary as a project.
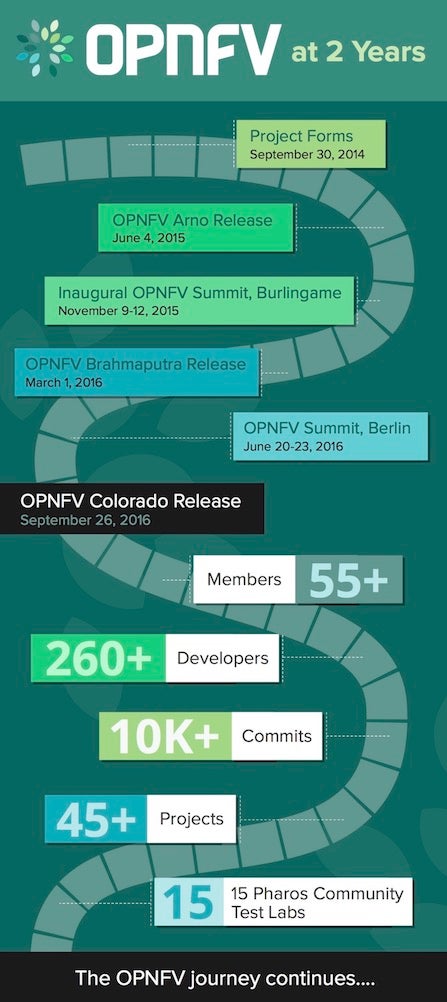
In the grand scheme of things, two years is not very long, but I am constantly amazed at how far the community has come in such a short time. For example, we’re now 53+ members strong (with many actual end users); we’re comprised of 47 approved projects; we’re running 15 operational OPNFV test-bed infrastructure labs (via the Pharos Project); we have three platform releases under our belt; and our developer force is over 260 and growing. This is no small feat, especially for a project with the formidable challenge of working upstream to assemble and test an open source NFV platform to help transform the industry.
 However, our progress has not come without challenges. In fact, when OPNFV first formed, we really weren’t sure if what we’re trying to do—orchestrate an entire industry to collaboratively create an open source NFV platform—would actually work. It’s an extremely daunting task, and, like any two-year-old, we are still trying to figure out the world around us and how to interact with it. While we’re feeling a bit more confident in our processes (e.g.,our recent Colorado release was delivered on the original release date) and are beginning to deliver real value into the open source ecosystem, there is certainly still work to be done (and, on occasion, we may suffer from a skinned knee). Things like refining our release processes, enhancing CI/CD, and delivering faster and better feedback to our upstream communities are crucial—along with longer-term goals like MANO integration and how we interact with technologies like Containers and IoT.
However, our progress has not come without challenges. In fact, when OPNFV first formed, we really weren’t sure if what we’re trying to do—orchestrate an entire industry to collaboratively create an open source NFV platform—would actually work. It’s an extremely daunting task, and, like any two-year-old, we are still trying to figure out the world around us and how to interact with it. While we’re feeling a bit more confident in our processes (e.g.,our recent Colorado release was delivered on the original release date) and are beginning to deliver real value into the open source ecosystem, there is certainly still work to be done (and, on occasion, we may suffer from a skinned knee). Things like refining our release processes, enhancing CI/CD, and delivering faster and better feedback to our upstream communities are crucial—along with longer-term goals like MANO integration and how we interact with technologies like Containers and IoT.
But today is about reflection on and celebration of what we’ve accomplished on this incredible journey. We’ve asked several of the original OPNFV founders to share their perspectives on how our community has evolved over the past two years and here’s what they had to say.
Chris Donley, Huawei
“Two years ago, I joined OPNFV because I believed in its potential as an open source project to develop and disseminate NFV solutions. In essence, “many hands make light work,” and everyone in the industry could play a part in creating a shared framework for the next evolution in networking. Two years later, we have successfully developed three releases and made a tangible impact on upstream projects. We have also made significant progress building our testing infrastructure through the Pharos project and our Plugfest events. Going forward, I believe that testing will become an increasingly important way to demonstrate OPNFV’s value proposition as it will help demonstrate interoperability across solutions and build confidence that OPNFV solutions are being faithfully adopted. I look forward to the next two years.”
Tetsuya Nakamura, CableLabs
“To be honest, I couldn’t imagine how far the community would progress when we initiated OPNFV two years ago. I hoped that OPNFV would become a place where the telecom industry and IT open source communities could meet together to understand how NFV/SDN works in practice, and influence the relevant upstream projects and the ETSI NFV-ISG. Now, I can talk with many open source engineers whom I had never seen before. Also, several commercial issues such as VNF lifecycle management and license management have been raised and started to be discussed. We are still only halfway through NFV realization, and given the fact that interoperability is critically important for NFV, OPNFV should remain at the center of this open source integration endeavor.”
Sandra Rivera, Intel
“Two years ago, OPNFV was a promise of open collaboration and an open source project to accelerate NFV realization. Today, OPNFV is living up to its promise and has become the defacto NFV framework standard for network operators. In the past year, the community has made significant progress towards enabling NFV functionality, promoting use cases, and implementing interoperability testing. A few highlights include:
- The first major interoperability testing conducted at our May Plugfest , where the community demonstrated multi-vendor interoperability for NFV applications running on standard server platforms.
- Extending our work into MANO, a major milestone towards building a complete stack that can be deployed in an operator environment.
- Addressed barriers to adoption by reducing latency with real-time virtualization capabilities, making performance much more deterministic.
As we continue to build on the promise and progress, I’m looking forward to developing additional functionality like Service Assurance and enhanced telemetry for real-time monitoring and analytics. Network operators have indicated that these capabilities are critical to running real-world deployments, and we’ll continue to work with the community to include these in future releases. We are inspired by what we’ve accomplished together, and are proud to continue the journey with you.”
Prodip Sen, HPE
“A little over two years ago we came together to build an open source organization with a purpose—to launch an industry implementation effort that would accelerate the development and adoption of NFV. Many of us were woefully ignorant of what open source entails, and we did not come to the table with existing code bases that were to be integrated. Rather, we had an architectural framework and some ideas. From that point, in two short years (believe me they do feel short), we have just completed our third software release, Colorado, which has been validated for 37 deployable scenarios. Just look at the statistics in the the chart to the right and you’ll get the idea—we are a healthy, productive, vibrant community.”
“As we move into the third year, we are expanding beyond our initial (self-imposed) constraints. OPNFV now has working groups focused in the areas of Infrastructure, MANO, Testing, and Security. Our cooperation with existing and newly formed upstream open source projects—e.g., OpenStack, ODL, Open-O—is increasing, and we are starting up projects that address operational and performance issues. We have a newly formed End User advisory Group whose members include participants from the cable and financial industries. As we have demonstrated quite effectively already, we intend to be an enabler in the networking transformation journey—and a partner who can be relied upon. There are more busy years ahead!”
In closing, I also want to thank our vibrant community, which is by far our greatest asset. As I told Linux.com in August, the telecom industry is used to working in standards bodies where competitors join forces toward a common aim, but the level of collaboration required to develop implementations in an open source project is even higher. People who want to see different solutions are supporting the broader community and helping all to move forward, realizing that we all benefit from the work. I’ve been completely delighted in the spirit of community that this group has fostered in its time so far. For an industry that is very new to the world of open source, we have definitely hit the ground running.
Learn more about getting involved with OPNFV.
—
About the author of this post
 Heather Kirksey
Heather Kirksey
Heather Kirksey
Director, OPNFV

 Lincoln Lavoie
Lincoln Lavoie

 Tapio Tallgren
Tapio Tallgren However, our progress has not come without challenges. In fact, when OPNFV first formed, we really weren’t sure if what we’re trying to do—orchestrate an entire industry to collaboratively create an open source NFV platform—would actually work. It’s an extremely daunting task, and, like any two-year-old, we are still trying to figure out the world around us and how to interact with it. While we’re feeling a bit more confident in our processes (e.g.,our recent Colorado release was delivered on the original release date) and are beginning to deliver real value into the open source ecosystem, there is certainly still work to be done (and, on occasion, we may suffer from a skinned knee). Things like refining our release processes, enhancing CI/CD, and delivering faster and better feedback to our upstream communities are crucial—along with longer-term goals like MANO integration and how we interact with technologies like Containers and IoT.
However, our progress has not come without challenges. In fact, when OPNFV first formed, we really weren’t sure if what we’re trying to do—orchestrate an entire industry to collaboratively create an open source NFV platform—would actually work. It’s an extremely daunting task, and, like any two-year-old, we are still trying to figure out the world around us and how to interact with it. While we’re feeling a bit more confident in our processes (e.g.,our recent Colorado release was delivered on the original release date) and are beginning to deliver real value into the open source ecosystem, there is certainly still work to be done (and, on occasion, we may suffer from a skinned knee). Things like refining our release processes, enhancing CI/CD, and delivering faster and better feedback to our upstream communities are crucial—along with longer-term goals like MANO integration and how we interact with technologies like Containers and IoT. Heather Kirksey
Heather Kirksey Chris Price
Chris Price
 Luke Hinds
Luke Hinds John Healy, General Manager, Software Defined Networking Division, Datacenter Solutions Group at Intel, will deliver a keynote at the Berlin OPNFV Summit. Prior to the event, we engaged with John to get his thoughts on the latest developments and future direction for the community project.
John Healy, General Manager, Software Defined Networking Division, Datacenter Solutions Group at Intel, will deliver a keynote at the Berlin OPNFV Summit. Prior to the event, we engaged with John to get his thoughts on the latest developments and future direction for the community project.
 Tetsuya Nakamura
Tetsuya Nakamura Susan James, head of Product Line NFV Infrastructure, Business Unit Cloud & IP, Ericsson, will deliver a keynote at the
Susan James, head of Product Line NFV Infrastructure, Business Unit Cloud & IP, Ericsson, will deliver a keynote at the